Understanding Product Risk Management In Today's Business Reality
Let's get one thing straight: product risk management isn't about filling out forms just to say you did it. It's the active, ongoing practice of protecting your business from the very real threats that can derail a product, tarnish your brand, and make your revenue disappear. It's the difference between navigating a sudden market shift with confidence and being blindsided by a supply chain failure that halts production for weeks.
Think of it less as a defensive shield and more as a competitive edge. When you get it right, it brings a crucial layer of foresight into your decision-making. The most successful companies don’t just react to problems; they anticipate them. They see risk management as a tool for asking better questions: What if our key supplier faces a natural disaster? What if a social media backlash erupts over a new feature? What if a competitor’s move makes our core value obsolete overnight?
The Evolving Nature of Product Risks
The days of simple, isolated risks are long gone. Today's threats are deeply interconnected and constantly morphing, which is why traditional, static approaches often fall short. A global risk report from the World Economic Forum, built on insights from over 900 experts, paints a picture of a fractured global outlook. It’s shaped by everything from geopolitical conflicts and trade tensions to the sheer speed of technological change.
These aren't abstract ideas; they create real operational vulnerabilities. They pile modern challenges like misinformation and extreme weather events on top of classic business risks. You can explore the full findings to get a deeper sense of this shifting landscape. This new reality requires a more dynamic view of product risk management. For instance, what looks like a purely technical risk, like a software vulnerability, is also a marketing risk (brand damage), a legal risk (data privacy non-compliance), and a financial one (potential fines and customer churn). To better prepare for these challenges, you can find essential insights in this guide to software development risk management.
Ready to drive more growth & achieve bigger impact?
Leverage my 25+ years of successes and failures to unlock your growth and achieve results you never thought possible.Get Started
Shifting from Old-School to Modern Risk Awareness
To really get a handle on this, it helps to contrast the old way of thinking with the new. Traditional risk categories were often predictable and neatly siloed. Modern risks, however, are multifaceted and pop up from the most unexpected places.
I've put together a table to show what I mean. It contrasts the conventional risks we're used to with the modern threats that product teams now face.
| Risk Category | Traditional Risks | Modern Risks | Impact Level |
|---|---|---|---|
| Market Risk | Direct competitor pricing | Viral social media criticism | High |
| Operational Risk | Equipment failure | Supply chain cyber-attack | Critical |
| Technical Risk | Software bugs | AI model bias | High |
| Regulatory Risk | Industry safety standards | Evolving data privacy laws (e.g., GDPR, CCPA) | Critical |
As you can see, the game has changed. A simple pricing war is one thing, but a viral negative campaign on social media can do far more damage in a fraction of the time. Likewise, a bug in your software is a problem, but bias baked into an AI model can have massive ethical and reputational consequences.
Recognizing these modern, interconnected threats is the first step toward building a resilient product strategy. It's about moving from a passive, checklist-based mentality to an active, strategic function that not only protects your company but helps it thrive in an uncertain world.
Building Your Risk Detection System Before Problems Surface
Most companies are reactive when it comes to risk, playing defense only after a crisis is already underway. But great product risk management flips that script. It’s not about waiting for alarms to sound; it’s about building a proactive system that actively hunts for threats before they can do any real damage. The most successful leaders I've talked to don't just check a "risk management" box—they cultivate an always-on, early-warning system that spans their entire product world.
This "system" isn't a piece of software; it's a cross-functional team. Your engineers, marketers, legal experts, and customer service reps are your front-line sensors. Each group brings a unique point of view that can light up blind spots you never knew you had. An engineer might spot a potential scalability issue down the road, while a customer support agent hears the first whispers of user frustration with a new feature.
Assembling Your Risk-Sensing Team
To make this work, you have to look beyond the formal org chart. Think about who truly understands the moving parts of your product and its place in the market. This often means creating a council—formal or informal—with people who can offer diverse insights.
- Engineering & QA: These folks live and breathe the technical side. They understand technical debt, infrastructure limits, and software vulnerabilities. They are your first line of defense against risks related to performance, security, and scalability. To help them spot problems early, an ultimate mobile app testing checklist can provide a structured way to identify potential issues before they ship.
- Marketing & Sales: This team has its finger on the pulse of market perception and what the competition is up to. They can alert you to brand reputation risks or sudden shifts in customer demand that could make your product less relevant.
- Customer Support: They are on the front lines, hearing directly from users. They’re the first to know when a product isn't meeting expectations, providing raw, unfiltered feedback about usability problems or unmet needs.
- Legal & Compliance: This group keeps an eye on the regulatory horizon. They can spot potential trouble from changing laws or industry standards long before they become expensive compliance headaches.
Bringing these different voices together gives you a much richer, more complete picture of your risk landscape. This Wikipedia entry on risk management shows a standard process flow, but the real power comes from populating each step with these cross-functional perspectives.

The framework itself is straightforward. Its power is multiplied when your "identification" step includes input from marketing, legal, and support, not just the technical team. This collaborative approach turns a theoretical process into a dynamic, company-wide defense mechanism. It's about creating a culture where anyone feels empowered to pull the "Andon cord" and raise a concern—not as a pessimist, but as a guardian of the product's success. This is a fundamental part of a mature product risk management strategy.
Smart Risk Assessment That Cuts Through The Noise
So, you’ve brainstormed a list of things that could go wrong. Now what? The real work begins here, with a smart risk assessment. It’s easy to fall into the trap of treating every potential issue like a crisis, but that’s a surefire way to exhaust your team and your budget. Effective product risk management isn't about finding every single threat; it's about accurately judging which ones can cause real damage and focusing your energy there.
The key is to evaluate each risk along two main lines: how likely it is to happen (probability) and how bad it will be if it does (impact). A minor typo on an obscure settings page is a low-probability, low-impact risk. A critical security flaw in your payment gateway? That's a high-probability, high-impact nightmare. Your job is to tell the difference and act accordingly.
A Practical Framework for Prioritization
To get past simple gut reactions, you need a consistent way to score these risks. A classic risk matrix is perfect for this. It’s a simple tool that helps you and your team visualize where each threat lands on the priority scale.
This infographic lays out a basic but powerful 2x2 grid for plotting risks based on their likelihood and potential damage.
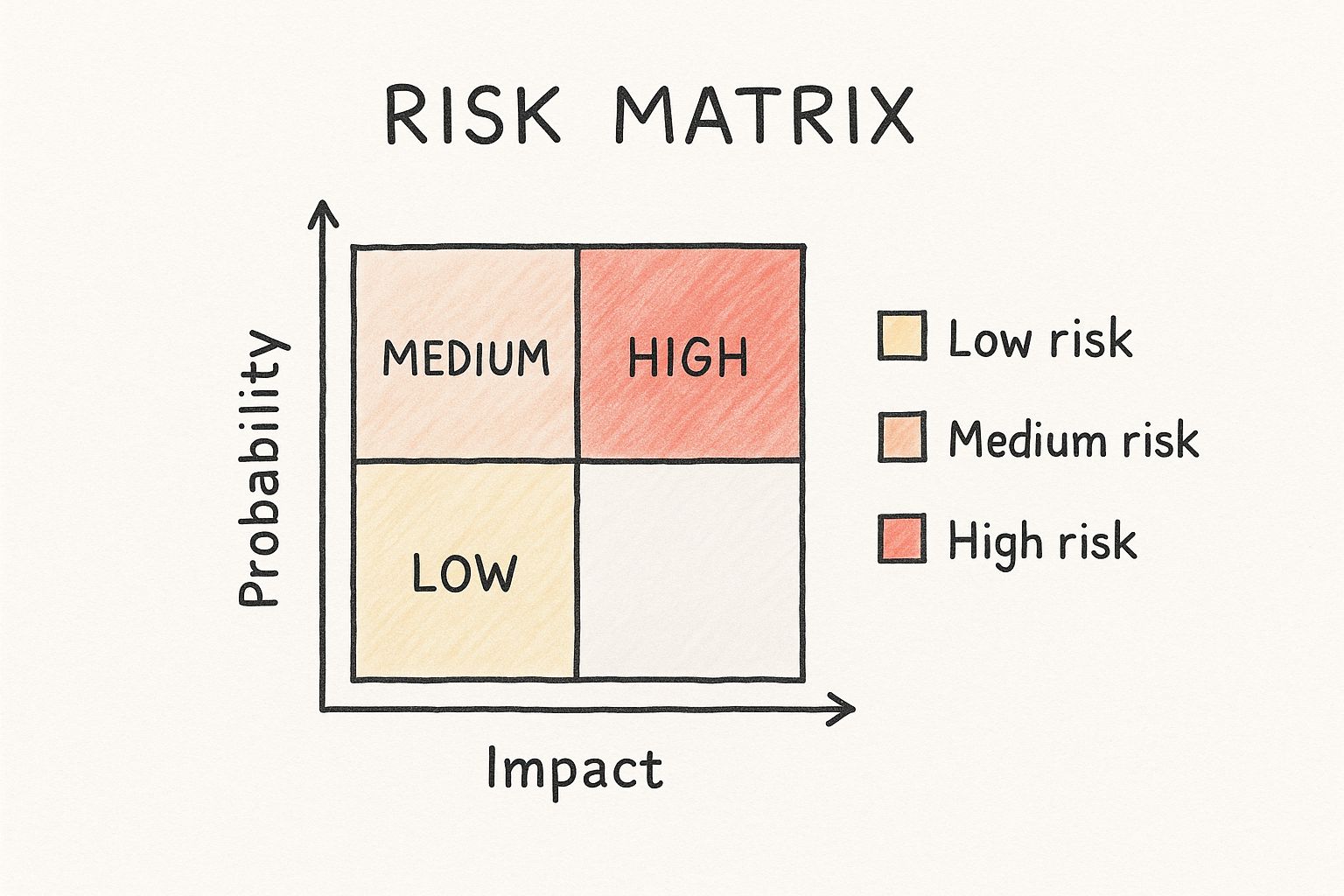
As the grid clearly shows, anything in that top-right quadrant (high-impact, high-probability) needs your immediate attention. Risks in the bottom-left corner can often be accepted or just monitored without taking up too many resources. This approach ensures you’re applying your limited time and effort where it truly counts.
To make this more concrete, here's a risk assessment table showing how you might score different types of product risks. It breaks down the probability, impact, and a final priority score to help you sort through the noise.
Risk Assessment Matrix with Real-World Examples
Practical risk scoring framework showing probability, impact, and priority levels for common product risks
| Risk Type | Probability | Impact | Priority Score | Example Scenario |
|---|---|---|---|---|
| Technical Risk | High (4/5) | High (5/5) | 20 | A major cloud provider outage takes your entire platform offline during peak business hours. |
| Market Risk | Medium (3/5) | High (5/5) | 15 | A well-funded competitor launches a similar product with a more aggressive pricing model. |
| User Adoption Risk | High (4/5) | Medium (3/5) | 12 | A redesign of the main user dashboard confuses long-time customers, leading to a spike in support tickets and negative reviews. |
| Financial Risk | Low (2/5) | High (5/5) | 10 | Unforeseen regulatory changes in a key market require a costly and immediate product overhaul. |
| Operational Risk | High (4/5) | Low (2/5) | 8 | A key third-party API for a non-critical feature becomes unreliable, causing intermittent functionality. |
| Legal Risk | Low (1/5) | High (5/5) | 5 | An obscure patent troll files a lawsuit, creating a legal distraction even if the claim is baseless. |
This table demonstrates how a simple scoring system can instantly clarify your priorities. A risk with a score of 20 is a "drop everything and fix this now" problem, while a risk with a score of 5 can probably wait.
Overcoming Internal Barriers to Objective Assessment
Using a structured framework like this is essential because our own biases can mess with our judgment. We often worry about dramatic, headline-grabbing events while ignoring the more boring but far more likely operational hiccups. This is why getting your whole team on board with the process is so critical.
The data backs this up. While 36% of companies plan to invest more in risk management, a shocking 87% of risk professionals feel their methods aren't fully embraced by their colleagues. You can discover more insights about risk management trends to see how widespread this issue is. This gap shows just how hard it can be to make risk assessment a shared, objective part of the company culture. A solid framework helps anchor these important discussions in data, not just opinions, making your entire product risk management strategy stronger and easier to defend.
Creating Risk Protection Strategies That Actually Work
Once you’ve separated the genuine threats from the background noise, the real work begins: turning those insights into robust protection strategies. A list of prioritized risks is useless without a clear plan to address them. Effective product risk management hinges on deploying the right response for each threat, making sure your efforts are proportional and practical. It’s a delicate balance, but one that’s crucial for protecting your product without stifling its growth.
Your response playbook essentially has four core moves: avoid, reduce, transfer, or accept. Each has its time and place, and knowing which one to use is a key skill. These aren't just theoretical options; they are strategic choices with real-world consequences for your product's future. The right leadership is essential for making these tough calls. If you're looking to sharpen your ability to guide teams through these decisions, exploring crucial technical leadership skills is a great place to start.
The Four Pillars of Risk Treatment
Deciding how to handle a risk is less about a rigid formula and more about strategic judgment. Your goal is to choose the most cost-effective and resource-efficient approach that lines up with your business objectives.
- Avoidance: This is the most direct approach—you eliminate the risk by not engaging in the activity that causes it. For example, if launching a feature in a new country comes with insurmountable regulatory hurdles and privacy risks, you might decide to avoid that market altogether. It’s a powerful but blunt instrument, often reserved for high-impact, high-probability risks where the potential downside far outweighs any potential gain.
- Reduction (or Mitigation): This is where most of your effort will likely be focused. You take active steps to lower the probability or impact of a risk. Think of it as adding safety measures. If you identify a single point of failure in your supply chain, you might mitigate that risk by onboarding a secondary supplier. For a software product, this could involve extensive security testing to reduce the chance of a data breach.
- Transfer: Sometimes, the best move is to let someone else handle the risk. This usually involves shifting the financial consequences to a third party. The classic example is buying insurance. A company might purchase cybersecurity insurance to transfer the financial impact of a data breach. You can also transfer risk through contracts, like including indemnity clauses with your vendors.
- Acceptance: This strategy might feel passive, but it's an active and important choice. For low-impact, low-probability risks, the cost of mitigating them might be greater than the cost of letting them happen. For instance, the risk of a minor cosmetic bug on a rarely visited settings page is often one you consciously accept. You acknowledge it, document it, and move on to bigger priorities.
This screenshot from ISO 31000, the international standard for risk management, visually outlines how risk treatment is a central part of the overall process.

The graphic shows that after identifying, analyzing, and evaluating risks, the "risk treatment" phase is where decisions are made and actions are implemented. It’s the critical step that bridges insight and action, turning your assessment into a tangible plan.
Monitoring Systems That Catch Problems Before They Explode
Even the most brilliant risk protection strategy is just a document collecting dust if you can't see trouble coming. This is where your focus has to shift from planning to active monitoring. A truly effective product risk management program relies on systems that give you a real early warning, not a constant stream of false alarms that just leads to alert fatigue. It’s about building a responsive nervous system for your product, not just a loud, annoying smoke detector.
Your goal is to get ahead of the curve by tracking leading indicators—things that can predict problems—instead of just lagging ones, like customer churn, which only tell you about damage that's already been done.
Establishing Key Risk Indicators (KRIs)
Think of Key Risk Indicators (KRIs) as the canaries in your product’s coal mine. They are specific, measurable metrics that give you a heads-up when a risk is trending in the wrong direction. A great KRI doesn't just describe a problem after it's happened; it helps you see it coming.
For example, instead of just tracking the total number of customer support tickets (a classic lagging indicator), you could monitor:
- The rate of negative sentiment mentions on social media and in community forums. A sudden spike here could be the first whisper of a brewing PR crisis.
- An increase in API error rates for a critical integration. This could be an early sign that a third-party service is degrading before it fails completely.
- A drop in user engagement with a newly launched feature. This is a powerful leading indicator of adoption risk and potential user dissatisfaction.
Setting up these KRIs isn't a solo mission. It requires a deep, cross-functional understanding of what really drives your product's health. This proactive approach is becoming more crucial across all industries. In fact, the global risk management market is projected to grow from $12.09 billion in 2024 to an estimated $21.62 billion by 2029. You can discover more about this market growth, which shows just how much value companies are placing on these capabilities.
From Monitoring to Meaningful Response
Once your KRIs are defined, the real work begins: building a response protocol. When a KRI crosses a predefined threshold, what happens? Who gets the alert? What decisions need to be made right away? Having a clear, pre-agreed-upon crisis response plan is what separates calm, decisive action from chaotic scrambling.
For high-pressure situations where every second counts, I've seen teams use a simple decision-making framework to great effect:
| Action Level | Trigger Example | Immediate Response |
|---|---|---|
| Level 1: Monitor | A 5% increase in API error rates over 24 hours. | An automated alert is sent to the on-call engineering team for investigation. |
| Level 2: Escalate | A 20% spike in negative social media mentions. | The marketing and product leads are pulled together to assess the situation and draft a response. |
| Level 3: Activate | A critical security vulnerability is confirmed. | The full crisis response team, including legal and executive leadership, is activated immediately. |
Finally, after the dust settles on an incident, run a blameless post-mortem. The goal here isn't to point fingers but to understand why the failure occurred and how you can strengthen your monitoring and response systems. This approach transforms each crisis into a valuable learning opportunity, making your entire product risk management process stronger and more resilient for whatever comes next.
Building Risk Awareness Without Killing Innovation
Here’s the tightrope every leader walks: how do you get your team to take product risk management seriously without grinding innovation to a halt? It’s a delicate balance. If you're too rigid, you create a culture of fear where nobody wants to take a chance. If you're too loose, you invite disaster. The secret isn't more processes; it's about building genuine risk consciousness into your team's DNA.
This means shifting the conversation from risk as a blocker to risk as a strategic part of making decisions. You want your team to ask, "What's the smartest way to take this risk?" not "How do I avoid all risk?" True innovation rarely happens in a zero-risk environment. Your goal is to empower your team to take calculated, intelligent risks, not to stop them from taking any at all.
Making Risk Management Engaging, Not Burdensome
Let's be honest: nobody gets excited about filling out another compliance form. The key to overcoming this resistance is to make risk awareness a part of the everyday workflow, not a separate, dreaded task. I’ve seen great success with techniques that make this engaging.
One powerful approach is gamification. Instead of dry training sessions, create workshops where teams compete to identify the most creative (yet plausible) risks for a fictional product launch. You could award points for:
- Identifying a clever risk.
- Accurately assessing its potential impact.
- Proposing a smart mitigation strategy.
This turns a mundane exercise into a collaborative problem-solving game. It builds critical thinking skills without the drudgery.
Another effective method is using real-world case studies—both successes and failures from other companies. Discussing a competitor's public stumble due to a security flaw is far more memorable than a generic PowerPoint slide. This makes the consequences of poor product risk management tangible and real.
Cultivating Accountability at Every Level
Ultimately, building a risk-aware culture depends on leadership. It requires leaders who openly discuss their own risk assessments and are transparent about why some risks are accepted while others are mitigated. When team members see that raising a potential issue is valued—even if it’s later deemed a low priority—they feel psychologically safe to speak up. If you're looking to refine this kind of influential guidance, you can find valuable insights on developing your own unique leadership approach.
This creates accountability from the ground up. An engineer feels just as responsible for spotting a potential data privacy issue as the C-suite does for a market threat. This shared ownership ensures that your organization's risk awareness enhances, rather than hinders, your ability to move quickly and seize opportunities.
Your Product Risk Management Implementation Roadmap
Turning insights into action is where a product risk management strategy really starts to pay off. It’s time to move from theory to tangible results by building a practical roadmap that fits your business reality. A successful rollout isn’t a one-size-fits-all download; it’s a phased approach that respects your company’s size, resources, and all the other competing priorities you're juggling.
Let’s break down what this journey actually looks like.
Phase 1: Foundational Setup (Weeks 1-4)
The first month is all about laying the groundwork. You don't need to solve every potential problem at once. Instead, focus on creating a solid foundation for your product risk management program. Your initial checklist should be tight and achievable, centered on getting the core mechanics in place.
- Assemble Your Cross-Functional Team: As we've discussed, this means identifying key people from engineering, marketing, legal, and support. This isn't just about sending calendar invites; it's about securing their commitment and being crystal clear about their roles and responsibilities.
- Run Your First Risk Brainstorming Session: Use the frameworks we talked about earlier to guide a session focused on identifying an initial list of risks. At this stage, the goal is quantity and diversity of thought. Don't worry about perfecting the list just yet.
- Create Your Initial Risk Register: Document everything from the session in a simple spreadsheet or a dedicated tool. Your columns should include the risk description, its potential impact, and the person who brought it up.
Phase 2: Assessment and Prioritization (Weeks 5-8)
Once you have a raw list of potential risks, the next month is dedicated to analysis and focus. This is where you separate the critical threats from the background noise. I've seen many teams rush through this part, but taking your time here pays off big time. For leaders guiding this process, understanding team dynamics is essential. We have some great resources on product management leadership that can help you navigate this.
- Score Each Risk: Use a simple matrix—I like using a 1-5 scale for both probability and impact—to score every item on your register. This brings a level of objectivity to the conversation.
- Prioritize the Top 5-10 Risks: You can't tackle everything at once. Force the team to agree on a small number of high-priority risks that require immediate attention. This focus is what drives real progress.
- Assign Ownership: Every single prioritized risk needs a clear owner who is responsible for developing a treatment plan. This accountability is non-negotiable and is the key to making sure things actually get done.
Phase 3: Action and Monitoring (Ongoing)
This phase never truly ends. It’s about putting your mitigation plans into motion and establishing a continuous feedback loop. Your focus shifts from planning to doing, observing, and adapting.
- Develop and Execute Treatment Plans: For each of your top risks, the owner must outline a specific plan (avoid, reduce, transfer, or accept) with clear action items and deadlines.
- Establish Key Risk Indicators (KRIs): You need to define the specific metrics you'll track to monitor these risks over time. How will you know if your plan is working or if a risk is becoming more severe?
- Schedule Regular Review Meetings: Set up a recurring meeting, maybe monthly, to review the risk register, check the status of your action plans, and scan the horizon for any new or emerging threats.
This roadmap gives you a structured yet flexible path to embed product risk management into your day-to-day operations, ensuring it becomes a sustainable function that adds real value.





